We do newsletters, too
Discover tips, technical guides and best practices in our biweekly newsletter.
FAQs
A Non-Human Identity (NHI) is a digital entity that authenticates and authorizes access on behalf of applications, services, and devices—in other words, it is a construct used for machine-to-machine access and authentication.NHIs are important because they facilitate automated operations, ensure seamless integrations, and support cloud scalability. As the world becomes more connected through APIs, third-party integrations, and microservices—and as digital transformation and AI adoption accelerate—NHIs have grown exponentially, outnumbering human identities by a ratio of 20:1.
Common Non Human Identities:
- Service Accounts: Used by scripts or applications to perform tasks.
- Service Principals: Managed identities for cloud services, like Azure or AWS roles.
- Roles: Permissions assigned to applications or services to enable secure operations.
- Storage Access Keys: Credentials that grant access to cloud storage services.
- Applications: Identities assigned to software applications for authentication.
- Database Users: Credentials used by applications to access and interact with databases.
Authentication Methods for NHIs:
- Secrets: Confidential keys used for authentication and authorization.
- Certificates: Cryptographic credentials used for secure communications.
- SAS Tokens: Time-limited tokens granting access to storage services.
- Personal Access Tokens (PATs): Used for authenticating API requests.
- OAuth Tokens: Short-lived tokens that authenticate apps to access resources securely.
- Passwords: Credentials assigned to NHIs for authentication, though considered less secure.
Unlike human identities, which have a strong foundation with a clear source of truth, ownership, and central management—typically through Human Resources or IT (usually, Active Directory) and defined lifecycle management—NHIs are democratized, often lacking clear ownership, and their management process is fragmented:
- Scale – NHIs outnumber human identities by 20X due to automation, AI,...
- Creation & Management – Unlike human accounts, NHIs are often created on demand by developers or applications, without IT oversight.
- Lack of Ownership – NHIs frequently lack clear accountability, leading to security gaps.
- Authentication – NHIs rely on API keys, OAuth tokens, and certificates, whereas human users depend on MFA, SSO, and passwords.
- Security & Compliance Challenges – NHIs cannot leverage traditional security controls like PAM, MFA, or SSO, making them a prime target for cyber threats.
Managing NHIs is uniquely difficult due to:
- Massive Growth – NHIs proliferate across cloud, SaaS, and DevOps pipelines.
- Limited Visibility – NHIs often exist outside IT or security teams’ direct oversight.
- Complex Authentication – API keys, OAuth tokens, and certificates are harder to monitor, rotate, and secure.
- Fragmented Governance – NHIs are created across multiple teams, increasing security blind spots.
- Higher Risk Exposure – NHIs lack traditional guardrails, making them vulnerable to breaches and compliance violations.
A purpose-built NHI security solution is required to address these challenges by automating lifecycle management, enforcing least privilege, and providing full visibility.
NHIs are frequent targets in cyberattacks due to their privileged access and lack of traditional security controls. According to IBM Cost of a Data Breach Report 2024, The global average cost of a data breach increased by 10% within just one year, reaching USD 4.88 million—the largest annual rise since the pandemic.
NHIs are frequent targets in cyberattacks due to their privileged access and lack of traditional security controls. According to IBM Cost of a Data Breach Report 2024, The global average cost of a data breach increased by 10% within just one year, reaching USD 4.88 million—the largest annual rise since the pandemic.
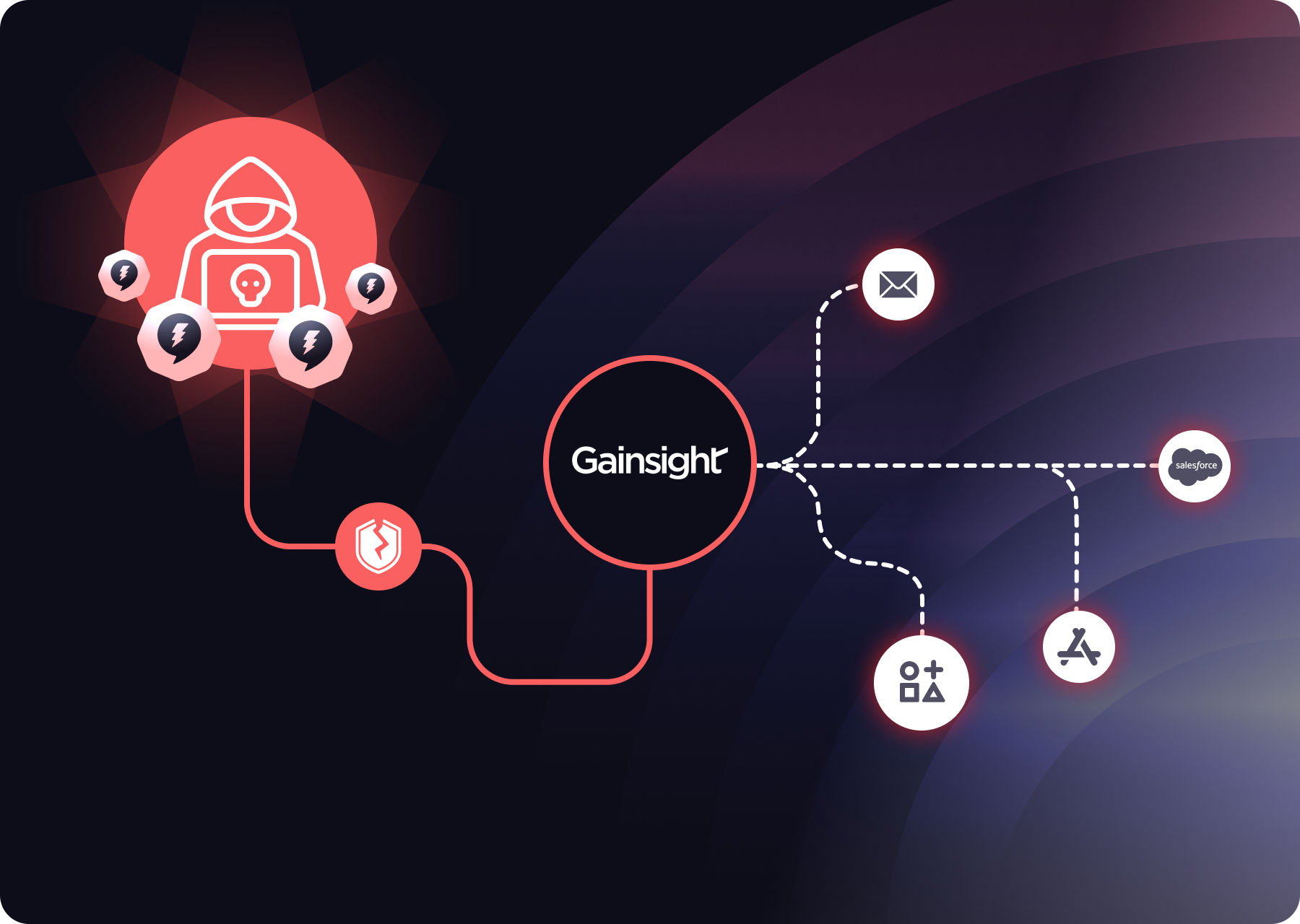
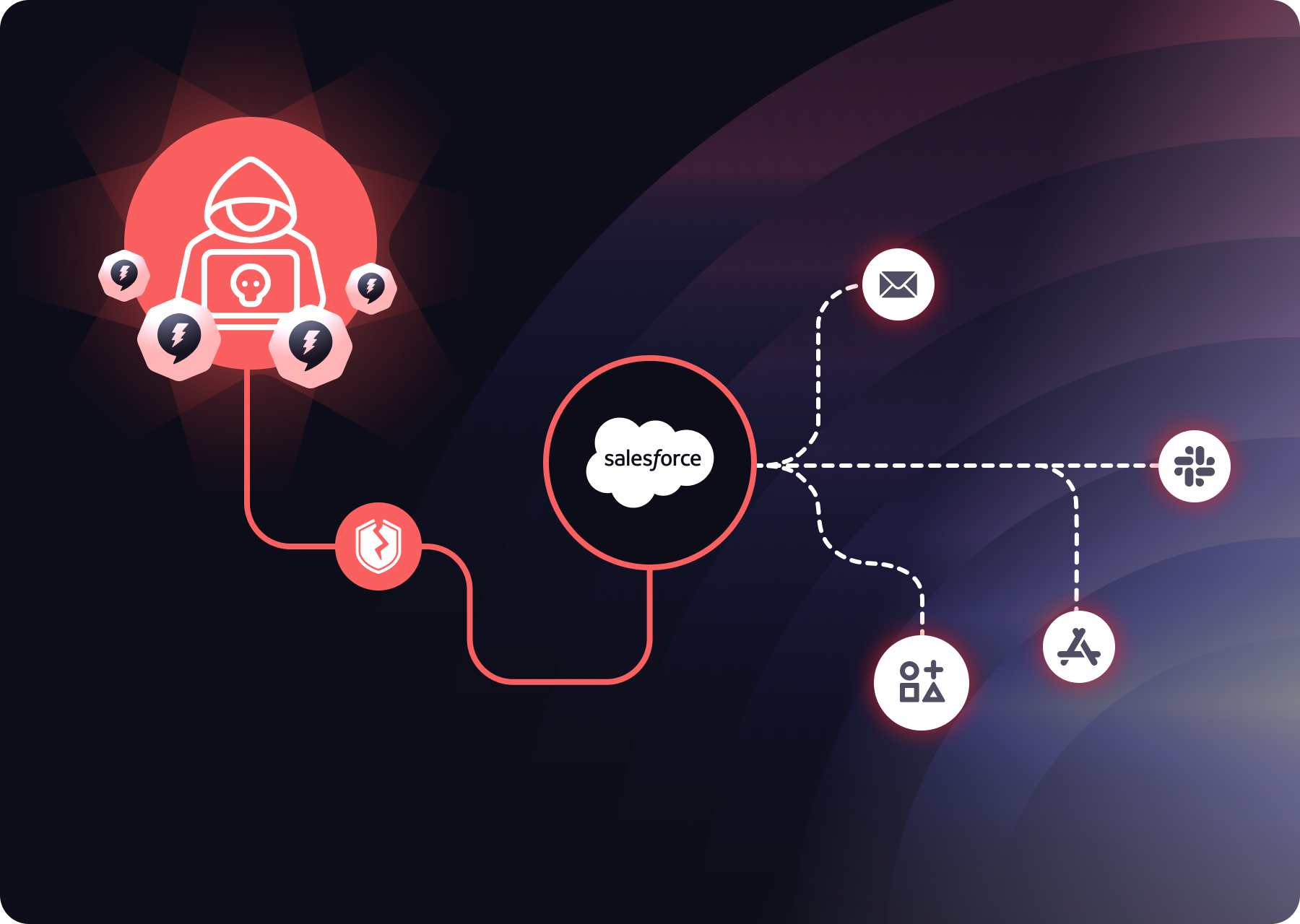
Recent breaches involving NHIs include:
- Microsoft AI Storage Breach – A misconfigured SAS token exposed 38TB of sensitive data.
- CircleCI Breach – Attackers compromised an OAuth token, affecting major enterprises.
- Mercedes-Benz Breach – Unauthorized access due to mismanaged service accounts.
These incidents highlight the risks of stolen credentials, lateral movement, and data exfiltration, making NHI security critical for compliance and threat mitigation.
A robust NHI security strategy requires a multidisciplinary team that includes IAM, cloud, security, IT, DevOps, and application teams. Their mission should be to establish leadership, conduct research, and implement structured NHI management strategies that focus on:
- Discovery – Identify all NHIs, including shadow and forgotten ones.
- Automation – Implement policy-driven lifecycle management to ensure security at scale.
- Monitoring – Continuously track NHI activities to detect anomalies and potential threats.
- Enforcement – Apply least privilege principles, enforce policies, and rotate credentials regularly.
By centralizing oversight and leveraging automation, organizations can ensure NHIs remain secure, compliant, and manageable at scale.
- Enforce Least Privilege – Limit access to only what's necessary.
- Use Strong Authentication – Prefer certificates and rotating API keys over static credentials.
- Regularly Audit Permissions – Identify and revoke unused or excessive access.
- Monitor NHI Activity – Use real-time security analytics to detect anomalies.
- Automate Everything – Manual processes can’t keep up with NHI sprawl.
Unmanaged NHIs can lead to:
- Data breaches from stolen credentials.
- Operational disruptions if critical service accounts fail or are misconfigured.
- Regulatory penalties for non-compliance.
- Lateral movement attacks, where attackers exploit NHIs to move deeper into your systems.
Think of unmanaged NHIs as open doors attackers are just waiting to find.
Zero Trust assumes nothing and verifies everything—including NHIs. Managing NHIs ensures every machine or service identity is authenticated, authorized, and continuously monitored. NHIs are a key pillar in a Zero Trust model because they’re often the first targets in lateral movement attacks.
The right solution should:
























.png)



















.png)





.png)
.png)




.png)

.png)

.png)






.png)









%2520Security_.jpeg)



