What are Non Human Identities?

A Non Human Identity (NHI) is a digital construct used for machine-to-machine access and authentication. NHIs are pivotal in today's evolving enterprise systems, especially as organizations transition towards machine-centric architectures. The need for rapid innovation has spurred the proliferation of microservices, 3rd-party services, and cloud-based solutions, creating a complex network where secure machine-to-machine access is governed by diverse NHIs that now form a vast ecosystem that outnumbers human identities by 10x-50x.
The landscape of NHIs is intricate, with definitions and constructs dependent on factors such as cloud providers, SaaS platforms, and on-premises systems. Cloud providers (AWS, Azure, GCP), SaaS (Snowflake, Databricks, Github, etc.), on-prem systems (ActiveDirectory, etc.) all use different models to create and manage NHIs. Unlike Human Identities, NHIs utilize a broader array of authentication mechanisms, lacking the security safeguard of Multi-Factor Authentication (MFA) commonly found in Human Identities.
Non-human identities are a crucial aspect of modern security frameworks and the identity stack, presenting a distinct paradigm from traditional human identities within organizational ecosystems.

Examples of Non-Human Identities
Examples of NHIs include Service Accounts, System Accounts, Application Accounts, and Machine Identities. Authentication methods for NHIs vary, incorporating secret information and federation mechanisms. Examples of authentication methods for NHIs encompass Secrets, Keys, Access keys, Certificates, and Tokens, each serving specific purposes in secure communication and authorization.
Special considerations arise in scenarios where identities are inseparable from the authentication string, as seen in Storage account access keys, Shared Access Signatures (SAS) tokens, and API keys for Software as a Service (SaaS) applications like Snowflake. In such instances, the authentication mechanism encapsulates permissions configuration, complicating identity management and access governance. As organizations continue to automate business processes with AI, the growth of Non-Human Identities is expected to accelerate, underscoring their critical role in the evolving landscape of enterprise systems.
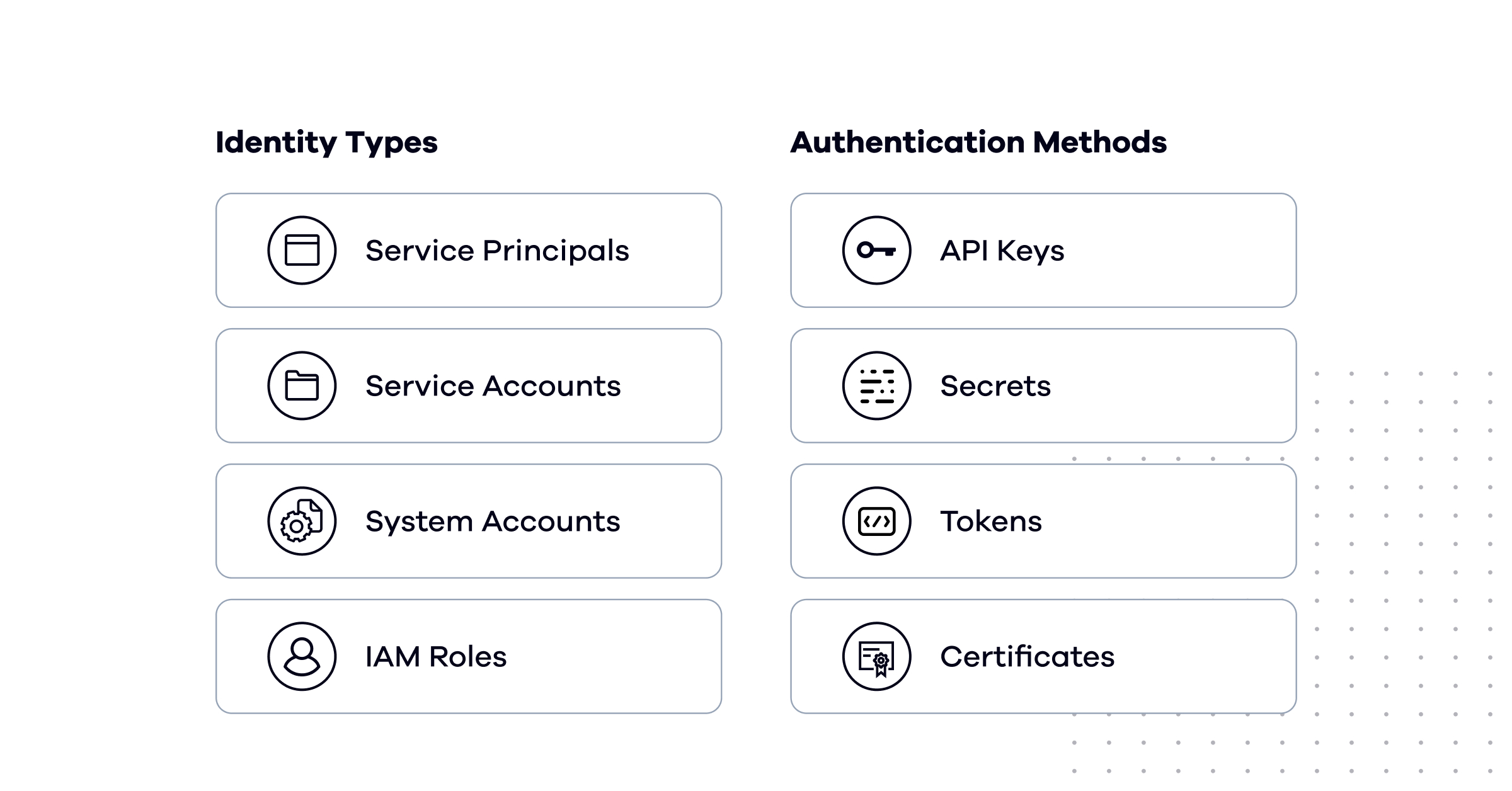
Human Identities vs. Non-human Identities
NHIs differ significantly from human identities in key aspects:
- Decentralization: NHIs are not centrally managed like human identities; instead, they are created and managed across multiple platforms by various stakeholders. It can be a real challenge to classify if a user is a human or a machine.
- Ownership: Unlike human identities, NHIs are not tied to specific individuals, evading regulatory requirements and often used by multiple administrators or applications.
- Scale: the large volume of NHIs (10x-50x more than human) creates a massive attack surface that is growing exponentially
- Rate of change: NHIs are subject to frequent creation and deprecation, aligning with the rapid pace of code evolution, rendering them more challenging to govern. However, it's worth noting that NHIs can also persist unchanged for years without rotation or imposed consumer limitations.
- Developer driven: unlike with Human Identities, the creation and control of NHIs aren’t centralized to IT or Identity Team. In many cases, NHIs are directly created by developers or even citizen developers in no-code low-code who may not be aware of their usage, as they represent the only means for the code they need to interact with systems
- Secret expiration: while frequent password rotation is very common around privileged users, many of the NHI are set to live for a very long time, and sometimes even without an expiration date.
- Operational Risk: Engaging with NHIs carries inherent operational risks. In the absence of a comprehensive understanding of all consumers, there is a potential for disrupting production systems. Moreover, efforts to rotate secrets may unintentionally disrupt established and vital business workflows.
- Authentication Diversity: NHIs support multiple authentication methods, reflecting technological evolution. Various systems may employ different authentication methods, leading to a wide range of approaches in use. The basic concept of Human Identity security relies on the fact that you can use these three factors to secure the authentication: 1) something you know (for example, password) 2) something you are (for example, face recognition) 3) something you have (for example, mobile phone) and then do multi-factor authentication. With NHIs the only protection is the secret that the user (in most cases a developer) gave to the machine - there is no SSO or MFA in the middle. This means that if attackers get hold of a Service Account and the secret there isn’t anything else that can stop them. In the cloud era, where APIs are the gatekeepers of access, identity becomes the new perimeter.

The need for Non-Human Identity Management solutions
Due to their characteristics and the nature of their lifecycle, NHIs pose several new operational challenges:
- How to discover and inventory all NHIs across cloud providers
- How to identify and prioritize violations and risks
- How to gain critical context metadata information, such as usage, dependencies, owners, consumers and resources accessed, to be able to remediate vulnerabilities without breaking things
- How to take control and automate of the lifecycle of new and legacy NHIs
Despite the risks, non-human identities are often blind spot for most enterprises because they lack the right tool for the job. Existing security tools in the stack, such as CSPMs, PAMs, Secret Managers, IAMs, were not designed to address the new lifecycle management requirements of NHIs and, as result, fall short of the goal leaving organizations vulnerable.
Given the unique operational challenges posed by NHIs, there is a pressing need for specialized Non-Human Identity Management solutions. These solutions should address key requirements, including discovery and inventory management, risk assessment, lifecycle automation, and developer readiness.
Oasis platform for Non-Human Identity Management is now available to close this gap. Oasis takes an NHI-first approach with purpose-built capabilities for discovery, inventory, posture assessment, lifecycle automation, and developer readiness.
Contact us for a free assessment of your environment
We do newsletters, too
Discover tips, technical guides and best practices in our biweekly newsletter.





.png)




