Secure Automation
and Prevent Disruptions
Energy companies depend on automation to drive efficiency and reliability across exploration, production, and distribution. Unsecured non-human identities (NHIs)—like service accounts and API keys—put these priorities at risk by exposing critical systems. Applications like SCADA for grid management or predictive maintenance tools can fail or leak data if NHIs are compromised. Oasis Security locks down these identities to prevent breaches, downtime, and compliance failures.

Benefits of Oasis
for the Energy industry
Protect critical infrastructure
Prevent costly downtime
Enhance compliance and risk management
NHI risks in the Energy sector
Compromised service accounts disrupt project management systems
Energy companies often rely on service accounts to access project management and design collaboration tools. If these NHIs are compromised, attackers can manipulate project data, delay timelines, or cause critical design errors, leading to project failures and reputational damage.
Hijacked machine identities interfere with industrial control systems
Many energy companies use automated machinery and industrial control systems (ICS) for operations. If attackers compromise NHIs tied to SCADA or DERMS, they could manipulate grid operations, cause cascading outages, or disrupt renewable energy distribution.
Compromised cloud credentials expose proprietary information
Energy companies store critical data such as energy distribution algorithms, predictive maintenance models, and infrastructure blueprints in the cloud. If attackers steal NHIs like API keys, they could manipulate or leak sensitive operational data.

Secure operations depends on secure NHIs
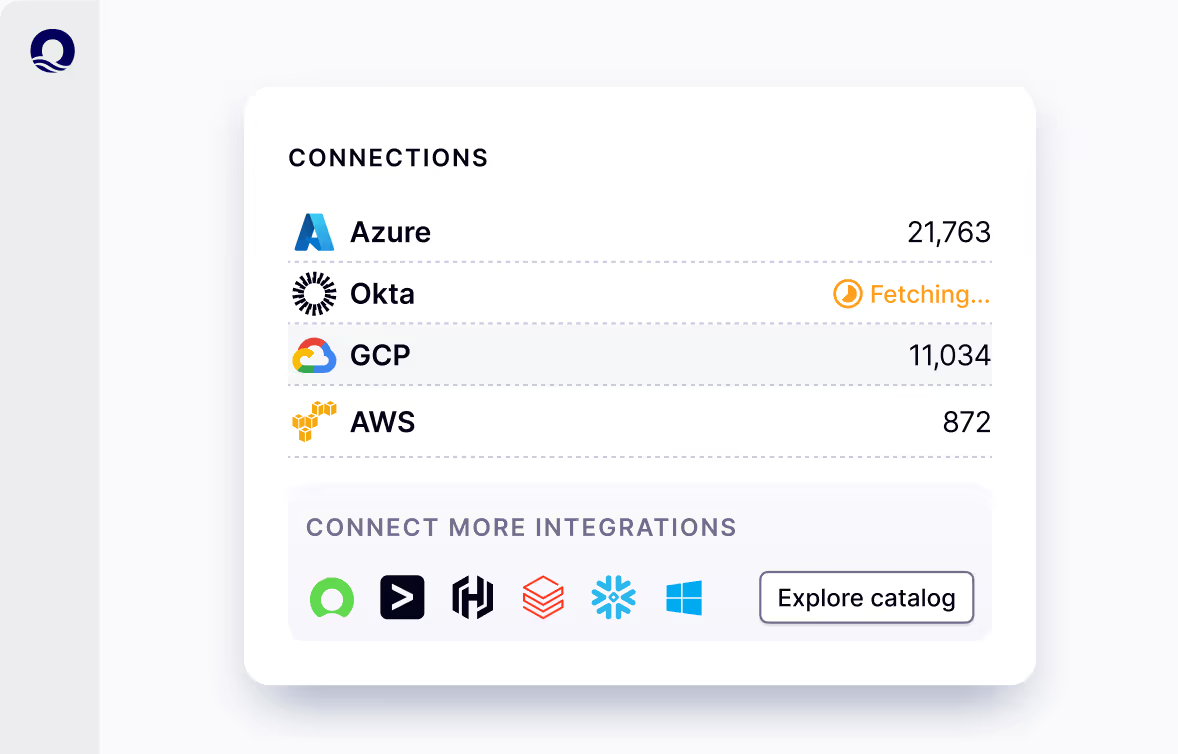

Ensure secure access to applications and data
Energy companies use specialized software for design, simulations, and project management. Oasis protects access to these critical applications by securing API keys, service accounts, and third-party identities, reducing the risk of credential misuse or unauthorized access.
Prevent operational disruptions
Unmanaged NHIs can lead to expired credentials, misconfigured systems, and unexpected downtime. Oasis proactively automates secret rotation and alerts about misconfigurations, ensuring that critical systems such as smart grids, energy control systems, and pipeline monitoring tools remain operational and secure.




Protect industrial control systems (ICS) and machine identities
Energy companies rely on industrial control systems (ICS) and automations for efficient operations. Oasis ensures that machine identities such as service accounts used to control these systems are secure, reducing the risk of unauthorized access.
See Oasis in action. Book a demo
Secure digital twins and smart infrastructure
Energy companies increasingly use digital twins and connected infrastructure for real-time monitoring and optimization. Oasis protects the data exchange between these systems, ensuring that only verified identities can access or modify operational parameters.
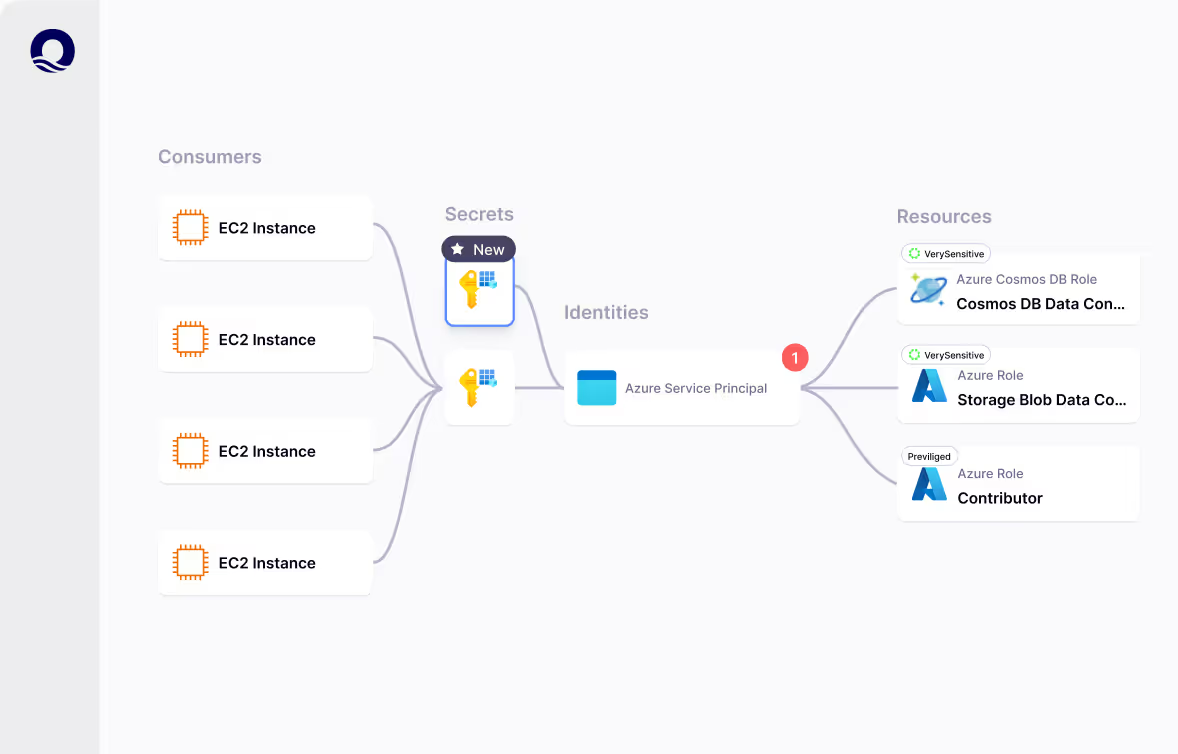



Prevent supply chain attacks
Modern energy projects rely on suppliers, contractors, and third-party software integrations. Oasis continuously monitors NHIs interacting with third-party systems, preventing unauthorized access and reducing the risk of supply chain attacks.
Meet regulatory and compliance requirements
Energy companies must comply with safety, data protection, and security regulations such as NERC CIP, FERC, and ISO 27001. Oasis provides audit logs, access controls, and automated policy enforcement to help organizations meet industry compliance standards with minimal overhead.







