Celebrating the first year of Oasis NHI Security Cloud

Cloud infrastructure service and SaaS have fragmented the identity perimeter as each service became its own identity provider. The adoption of DevSecOps practices has shifted security left, essentially circumventing centralized governance. The net effect has been an uncontrolled NHIs sprawl that created a massively largely attack surface. NHIs are everywhere, they outnumber human identities by a factor 20x on average, are highly privileged, and often unmanaged. Think CI/CD pipelines, third-party integrations, automation scripts, and cloud services each running on identities with powerful permissions and no oversight. AI is poised to pour more fuel to the fire.
Traditional tools weren’t designed for this world because they are bound to legacy human-centric data models and rigid, centralized governance models. At Oasis, we recognize that this new reality demands a new approach and this is why we built Oasis NHI Security Cloud.
How far we've come!
Our vision is to revolutionize identity security by leveraging powerful AI-based analytics and by implementing an infrastructure-agonistic lifecycle management control plane that unifies governance across systems without forcing centralization.
Over the last year, we focused our R&D efforts to drive four key outcomes for our customers:
- Better visibility both in terms of breadth and depth
- Stronger security eliminating risk exposure to vulnerabilities and threats
- Automating governance of otherwise, complex lifecycle management tasks
- Enhance our platform enterprise readiness for scalable operations

It seems just like yesterday that we started our journey, but it’s amazing to see how far we’ve come. In 12 months we shipped hundreds of new features, in this blog we want to take a minute to recognize and highlight the biggest milestone we accomplished.
Visibility. No blind spots. Every identity mapped, every secret discovered
- Support for all the most critical identity store providers, including Azure, AWS, GCP, Active Directory for on premise and Okta.
- Expanded coverage to unseen NHIs like secrets, API keys, access tokens, and database users, which are not managed in traditional IdPs but are critical for infrastructure security with integrations with various secret managers, vaults and CI/CD tools such as Github, Snowflake and HashiCorp.
- Oasis Context Graph. NHI world visibility isn’t just about inventory, it is also, and probably even more significantly about context. Context means understanding what identities have access to, what permissions they hold, who or what is consuming them, and who owns them. Our patent-pending Context Reconstruction Engine (CRE, aka. Sherlock) leverages the industry most powerful set of AI/ML, LLMs and behavioral algorithms to continuously correlate data from audit logs, IDP, Vaults, DSPMs, ASPMs, etc., providing the deepest business context map of each identity, providing the deepest business context map of each identity (class/type, usage, consumers, authentication methods, entitlements, resources)

Security: eliminate threats and vulnerabilities before they become breaches
- Automated risk posture analysis. From identifying critical posture violations such as unrotated secrets and overprivileged accounts to identifying threats and anomalies, operational issues and misconfigurations, our platform continuously monitors the environment to identify security policy violations providing a criticality score for prioritization of remediation.
- Threat Detection and Response for NHIs with Oasis Scout, powered by Authprint technology. A truly breakthrough tech enhances detection accuracy by matching anomalies to known threat actor patterns. This includes scanning for exposed credentials in cloud environments and repositories, along with leaked credential detection to help mitigate risks.
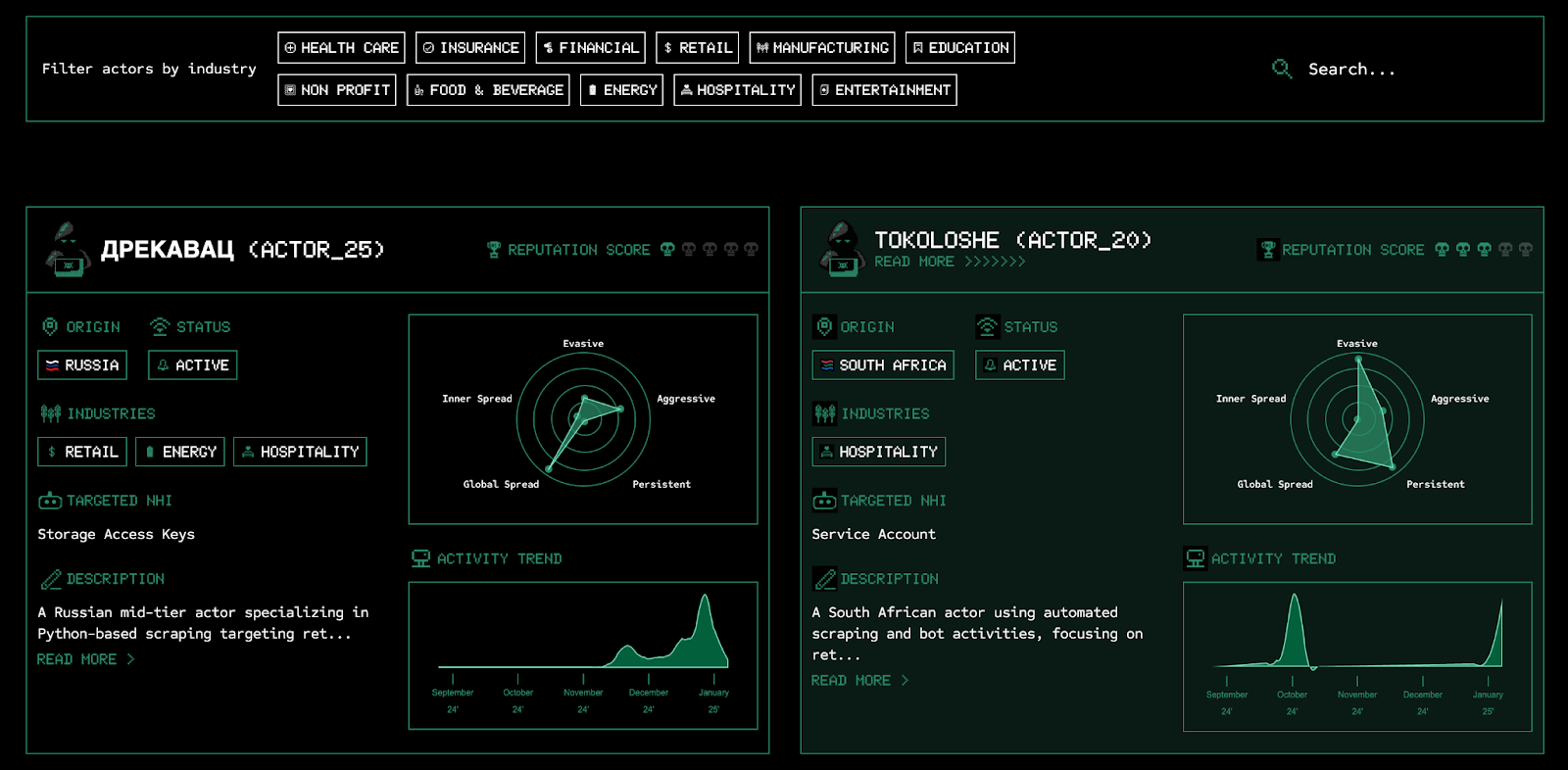
- We launched the Non-Human Identity Threat Center, a new resource that provides real-time threat intelligence on actors targeting NHIs. This resource focuses on mapping threat actors, fingerprinting their activities, tracking their movements across the cloud, and gaining a deeper understanding of their tactics, techniques, and procedures, enabling security teams to stay informed and proactive.
Governance and Identity Lifecycle

- Stale account safe decommissioning: To reduce the attack surface while upholding the principle of least privilege, Oasis NHI Security Cloud automatically identifies and verifies stale NHIs, triggering their safe decommissioning.
- Automated secret rotation: This year, we introduced secret rotation. Rotation is configured by the user via policy and executed by Oasis autonomously, ensuring company policies and best practices are consistently applied.
- Overprivileged: Enforcing least privilege is a must. Oasis detects overprivileged NHIs and generates tailored playbooks to remediate issues with the most effective solution for each case.
- Ownership and attestation: Ownership ensures oversight and accountability throughout the lifecycle of an NHI. Oasis automatically suggests and assigns responsibility for each NHI based on data from IdPs, logs, CMDBs, tags, metadata, and other sources. To keep this information current, Oasis NHI Cloud solution also offers attestation, a systematic review and verification of human ownership and usage of NHIs.
- Compliance: Oasis generates compliance-ready reports aligned with frameworks like PCI 4.0, NIST, and SOC 2, simplifying audits and reducing compliance fatigue.
Enterprise Readiness
- New UI for an improved user experience
- Integrations with DevOps and collaboration tools
- APIs for custom workflows
- Documentation portal to support customers with detailed resources
Our first year has been about laying the foundation, but we’re just getting started. In 2025, we’re focused on expanding automation, deepening integrations, and continuing to partner with our customers to tackle real-world challenges.
Thank you for being part of this journey. We’re excited for what’s ahead!
We do newsletters, too
Discover tips, technical guides and best practices in our biweekly newsletter.










